
Introduction
Whenever you visit a site, click on a link, or fill in an online form, a process begins where your browser retrieves and displays actual content. This process is called a web request and may appear to happen instantaneously, but involves genuine details of steps that happen quietly in the background. Developers, network engineers, and just curious users need to know what happens during a web request, which opens the window on the intricate dance between clients, servers, and networks that organises the web for all of us.
This article will cover each phase involved in a web request, starting from the instant you enter the URL in a browser and ending with the moment that the requested web page appears on your screen. This entails things like DNS resolution, HTTP protocol, server-side processing, and browser rendering. The aim of this project is to unveil the many mysteries attached to requesting a web page and paint a picture of appreciation for the complex systems that make that possible. Knowing something about the web request lifecycle will further help implement performant, reliable, and secure applications, be it a newbie or an experienced developer.
Step 1: Entering a URL and DNS Resolution
Translating the Domain Name to an IP Address
When the user types the URL in the browser’s address bar, say www.example.com, the web request process is initiated. Computers, however, cannot understand domain names; instead, they require IP addresses to find servers on the internet. This is where DNS, or Domain Name System, comes in. The DNS performs the function of a phonebook on the internet, translating the user-friendly domain names into machine-friendly IP addresses. Upon the user pressing enter, the browser first looks into its local cache of IP addresses to see if the IP address of the domain exists there. This DNS resolver can either be provided by the user’s internet service provider or may be from third-party DNS providers, such as Google and Cloudflare.
Then, this resolver will query the root name servers, then follow to the top-level domain (TLD) name servers, and finally it will go to the authoritative name server for the domain. Each check narrows down the search until the right IP address is found. This address is communicated back to the browser and held in cache for later use. While all these steps in DNS resolution may take milliseconds, they are crucial in linking you to the right web server. If anything goes wrong during this stage-e.g., the DNS records are misconfigured or the domain expired-, you may be receiving errors like “server-was-not-found.”
Optimizing and Securing DNS Queries
The efficiency and security of this whole DNS resolution process determine user performance and safety. DNS caching helps with this by storing domain names resolved previously at the browser or operating system level so that lookup times can be reduced. This means that every time you go back to the same website, your browser would not have to perform a full DNS resolution, resulting in faster access. With the help of CDNs, requests are rerouted to different servers, closer to the user, thereby ensuring a decreased latency and quicker response times.
But unfortunately, until now, most DNS queries have been unencrypted; hence, they can be easily monitored and even spoofed. With this background in mind, other protocols such as DNS over HTTPS (DoH) and DNS over TLS (DoT) have entered the scene to encrypt DNS queries for the purpose of user privacy. Such security enhancements can be harnessed by web developers and network administrators, such as DNSSEC usage, for assuring data authenticity and attestation against possible data spoofing. Other upgrades guarantee safe and effective access to end-users as an initial step, leaving more grounds to further strengthen what is probably the most credible step within the web request process.
Step 2: Establishing a TCP Connection and Sending the Request
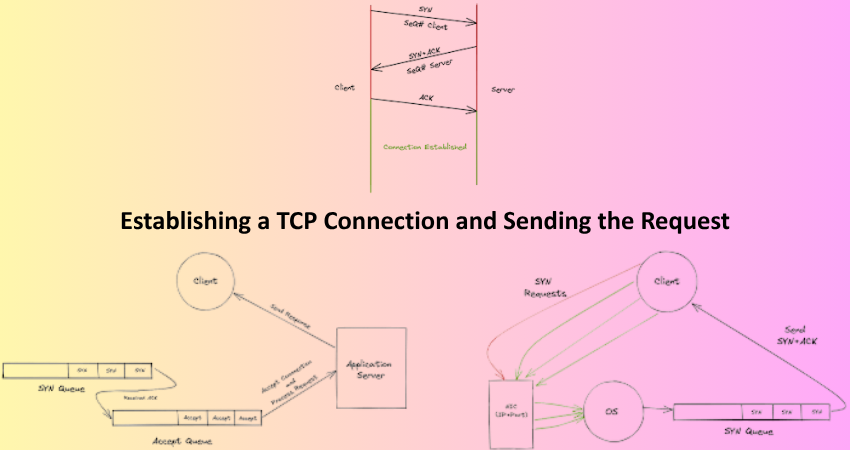
TCP Handshake and Port Communication
After working through an IP address, the user interface achieves a connection to the server via Transmission Control Protocol (TCP). This connection is mainly used for the data transfer between the client and server. TCP functions on the transport layer of the internet protocol suite, providing reliable, ordered, and error-checked delivery of a stream of data. Before anything can be transferred, the client and server have to do a three-way handshake. It is when the client sends a packet requesting synchronization (called SYN), to which the server replies back with a packet bearing SYN and acknowledgment (thus called SYN-ACK). Finally, the acknowledgment is received from the client regarding the server’s reply, which is sent as an acknowledgment (ACK) packet.
This handshake will make the connection stable at some port, normally port 80 in the case of HTTP and 443 for HTTPS. On establishing a connection, the client may immediately send an HTTP request to the server containing headers such as user-agent, accept-language, and cookies. In case of a POST request, or of a PUT request, the message consists of a body containing, for instance, form inputs or a JSON payload. Once the request reaches the server, it gets processed to determine which resource is being requested or which action needs to be taken on behalf of the client.
HTTPS and TLS Encryption
For secure communications, it does secure communication, and thus HTTPS is used, but not simple HTTP. HTTPS encrypts data transferred between client and server using Transport Layer Security (TLS). In this way, data is protected from evil hackers who want to intercept sensitive information, such as passwords or credit card numbers. During a TLS handshake, the client and server agree on the encryption algorithms to use and exchange cryptographic keys. The server presents a digital certificate, which the client verifies against trusted certificate authorities (CAs) to ensure the server is authentic.
Integrating TLS secures and authenticates data, ensuring that the material delivered for both parties has not been tampered with during transmission. Most current browsers show a padlock icon in the address bar during the use of HTTPS. Website owners must purchase SSL/TLS certificates and then configure their servers to enforce HTTPS with a common redirect of all traffic on HTTP. The requests have really become an entry to online life, especially for e-commerce, online banking, and those that require some sort of verification of users.
Step 3: Server-Side Processing and Response Generation
Web Server and Backend Application Execution
It is the arrival of an HTTP request that fires a web server to receive it. The application might be Apache, Nginx, or Microsoft IIS. The web server can, therefore, fetch the static contents such as HTML, CSS, and images and serve them without interference from any backend. If, in any case, the request is for dynamic content, the web server passes the request to the respective backend application. Technologies like Node.js, Python (Django/Flask), Ruby on Rails, Java (Spring), and PHP are used to build this application. Business logic can be applied in the backend application to fulfill the request, thereby interacting with database queries or potentially calling other services.
For example, a login process would require the user to enter credentials. Verification may include the backend checking some database for those credentials, creating a session for those credentials, and returning the user’s dashboard. Other parts of the request may have middleware components to log the request, validate the authentication tokens, and compress the responses. But that must happen fast, with users almost expecting an immediate response. A good server-side design in concert with a scaling infrastructure (microservices or serverless functions) to service many requests at once without degrading performance.
Database Access and API Communication
Dynamic web apps need databases on the backend for storage and retrieval of information. Whenever a request needs processing, it is passed to the backend to process the request for accessing data from a relational database, such as PostgreSQL or MySQL, or NoSQL solutions, such as MongoDB or Firebase. Proper and effective querying of the database is required; if queries are not done properly and indexing is weak, it can really slow down the response time. ORMs (Object Relational Mappers) like Sequelize, Hibernate, or Django ORM provide a good and efficient way to map application objects to database tables.
Databases aside, numerous applications procure third-party data from some external APIs for tasks such as payment processing and sending notifications. Such interactions must incorporate some error handling, retry, and caching mechanisms to ensure their reliability. The response is then assembled, primarily as JSON or an HTML string, depending on the original request parameters, and sent back to the client by the web server. The response header and status codes tell the browser the result of the request-whether 200 for OK, 301 or 302 for redirection, 401 for Unauthorized, or 500 for Internal Server Error.
Step 4: Receiving and Rendering the Response in the Browser
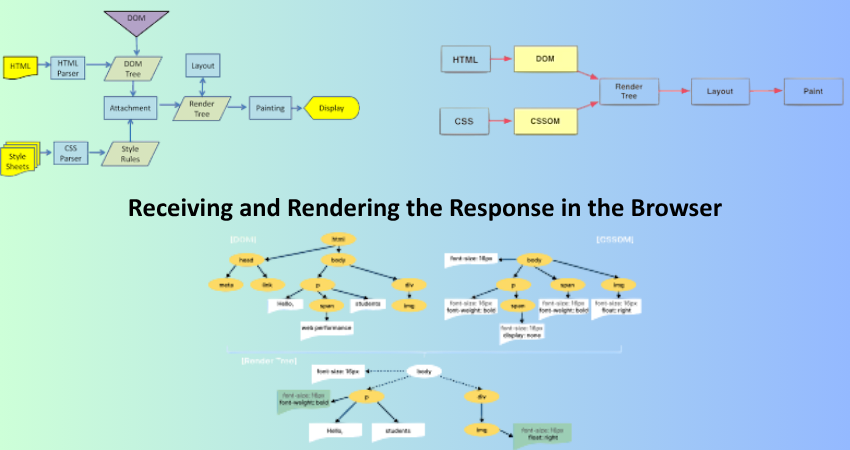
Interpreting the Response and Building the DOM
The client is now going to start rendering whatever he has received fa from the server. He’ll be parsing this whole document in HTML, the parsing stage actually builds the Document Object Model (DOM) as a tree-like structure that describes the contents and structure of the page: documents, images, text, and other objects. The site of handling the scripts is as follows: parse CSS to style elements within and layout elements in live space, render them live on the screen, and execute JS that may be inline or span various external files in the execution context, thus manipulating the DOM and resulting in the event or dynamic behavior of dropdown menus and other types of content loading without a page refresh, for instance.
Rendering is performed in phases, first the important ones like CSS within the <head>, and then all other deferred scripts. Techniques of browser optimization such as lazy loading, asynchronous script execution, and resource preloading were used to enhance performance. Monitoring of rendering performance for identifying rendering bottlenecks is done using Lighthouse or Chrome DevTools. It is an important part of the web request life cycle, as it greatly enhances usability and boosts SEO and engagement.
Handling Assets, Caching, and Errors
Modern website consists of fonts, images, videos, and other third-party scripts used to fetch each by the browser when it parses its HTML. To lessen the load time, the assets are cached inside the browser locally instead of downloading them each time a user visits a site again. The length of storage and possible need for revalidation are determined by the HTTP cache-control headers. A Content Delivery Network (CDN) distributes delivering assets through geographically distributed servers to minimize latency.
Types of problems such as broken links, missing images, or scripts that fail thus all have error messages sent to browsers with console log warnings. A few of the status codes that help describe the condition of data include HTTP status code such as 404-not found, 403-forbidden, and 500-interior server error. Custom pages can be created for error messages to make the experience better for the users and provide instructional purposes. Managing assets, caching strategy, and error handling create a smooth and robust experience on the web and also minimize disruption at the last stage of the request sent over to the web.
Conclusion
Comprehending what happens during a web request exposes the intricate operations of any alive website. Each step-from DNS resolution to browser rendering-is a set of protocols, software, and infrastructure each specialized to facilitate seamless delivery of content working in concert. With this knowledge, developers can sharpen their axe with regard to performance tuning, security improvement, and troubleshooting; thus, they can give users some insight into the unseen forces behind their day-to-day experience on the internet.
As the web continues to forge ahead through HTTP/3, the edge, and WebAssembly, it remains vital to ground oneself in web requests. From the process in which one develops a web application and tunes a server to understanding how the internet ticks, gaining mastery over the web request is tantamount to building a foundation of technical literacy and honing one’s skills in development.